SLAE Assignment 6: Polymorphic version of shellstorm shellcodes
Look I'm PushPopEAX, now I'm PushPopEBX
Hint: Its easier to read code on github !
Welcome back !
Today we will have to rewrite some shellcodes from shellstorm database. The idea is that the shellcode perform the exact same activity but with different opcodes and patterns. That way any system which tries to detect this shellcode using pattern or signature will be fooled.
example: An IDS trying to detect shellcode bytes over network will trigger an alert when it sniffs push "//sh" followed by push "/bin" x86 bytes instructions
Modified versions can come also with a cost : the original shellcode is probably optimized to be the shortest available chain of instructions so the resulting modified shellcode might be longer. As a rule of the exercise, we should not make it larger by over 150%. For your information, you can check the size of the instructions of a binary with "size" command.
Example : size $(which nc)
text data bss dec hex filename
22014 1168 456 23638 5c56 /bin/nc
One remark though: in the SLAE Course, this is called polymorphic version but I dare to disagree with this term. For me "polymorphic" means changing multiple times, not only one time (like the shikata_ga_nai encoder we have been analyzing). So I would call them rather modified version of shellcodes :).
Second remark: If you know a script or tool which can subsitute similar opcodes automatically then please put it in comments. I think it should be quite easy to code and can be useful for this kind of modification.
Rewriting the vanilla bread and butter shellcode
What is the most used shellcode ? Probably execve /bin/sh ones. Lets modify one then :] The original shellcode is shown in comment otherwise you can find originals ones inside the github repo. I will provide explanations in the code as usual.
Alright we should be able to avoid some patterns matching there. Let's go on !
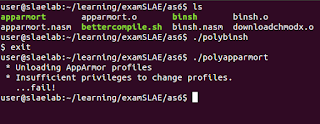
Making a dent inside the AppArmor
How about disabling some security protection like AppArmor ?Lets try our morphed versions, need to be sure they are still working as expected.
You can verify that modified shellcodes do not exceed size of the originals by more than 150% using size command.
Download and run goblinmod mkII
This is a quite useful shellcode we have here: download a file, make it executable and run it. Lets make our custom version but this time lets try to reduce the size of this shellcode ! (it grants extra points for the exercise). For instance instead of "XOR EAX,EAX" followed by "XOR EDX,EDX" we can use XOR EAX then CDQ. CDQ is only one byte opcode and as a side usage. it can put 0 into EDX. The overall operation size is decreased by one byte while doing so :]Lets test it quickly.
Good. You can check that the size is a bit smaller.
user@slaelab:~/learning/examSLAE/as6$ size downloadexec
text data bss dec hex filename
103 0 0 103 67 downloadexec
user@slaelab:~/learning/examSLAE/as6$ size polydownloadexec
text data bss dec hex filename
100 0 0 100 64 polydownloadexec
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
SLAE - 970



Comments
Post a Comment